
6 myths about MDM
In the bustling Silicon Valley, where digital transformation was the talk of the town, one tool emerged as the unsung hero in the pursuit…
Continue Reading
In the bustling Silicon Valley, where digital transformation was the talk of the town, one tool emerged as the unsung hero in the pursuit…
Continue Reading
“Cyber-Security is much more than a matter of it” This quote by Stephane Nappo explains the depth of cybersecurity and the amount of harm…
Continue Reading
Codeproof is a comprehensive mobile device management (MDM) solution that offers a wide range of features for managing and securing mobile devices. Some of…
Continue Reading
Installing a whole new Mobile Device Management (MDM) system to your SMB’s existing suite of systems is difficult. It requires taking an audit of…
Continue Reading
Last month, Twitter said it would allow its staff to work from home permanently if they want to. This is following a recent trend among big tech companies like Facebook…
Continue Reading
It’s with great pride that we would like to announce that Codeproof is now a T-Mobile Sell With partner. We will now market and…
Continue Reading
As the UEM/MDM/EMM industry is expected to grow in the next few years. Gartner has estimated that the adoption of Windows 10, Google Chrome OS, and Apple…
Continue Reading
MDM (Mobile Device Management), EMM (Enterprise Mobility Management), and UEM (Unified Endpoint Management) are often terms thrown about in the mobile security space without…
Continue Reading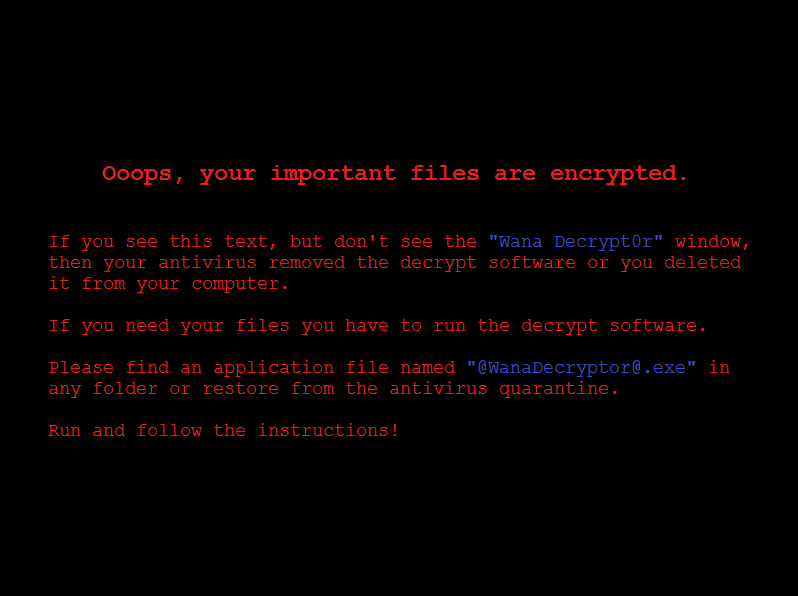
A few days ago, we witnessed the largest ever ransomware attack, which impacted over 230,000 individual computers across 150 countries. Cybercriminals exploited known vulnerabilities…
Continue Reading
Both iOS and Android come with features that are designed to further secure enterprise applications over and above the security level of standard consumer…
Continue Reading