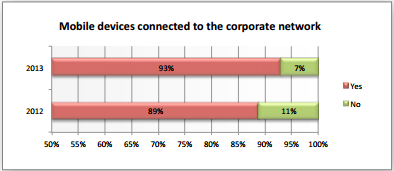
Our world is becoming more mobile. A few years ago, the Internet connected everyone across the globe to each other. The only problem – every person had to sit in front of their computer. The introduction of tablets and smartphones allows these connections to be filled regardless of where the person is at or what they are doing. As consumers demand greater mobility in their everyday lives, so do managers and employees. Dimensional Research reported in 2013 that 93% of companies had mobile devices connecting to their networks, including personal and company owned devices. This statistic was up 4% from the previous year. As the demand for mobility increases, corporations will need to address that demand accordingly within their IT strategies.
The greatest concern for most IT departments is the amount of corporate information found on mobile devices. The same report from Dimension mentions 53% of companies surveyed know of sensitive customer information on mobile devices. The problem inherent with this information being on these devices are they are mobile: meaning they are easier to lose or be stolen. So the advantages of mobility to a corporation may be its greatest detriment.
Security incidents involving mobile devices is on the rise as well with 79% of companies reporting such incidents. More than half of large companies had incidents exceeding $500,000 in costs. Businesses with less than 1000 are not immune with 45% citing incidents exceeding $100,000 in costs. The greatest threat with mobile security is not cyber criminals, but the mobile user.
Risks for Mobility in the Workplace
Risks with Devices

Variety propels the demand for mobility devices. A consumer can choose between phones, tablets and laptops from different manufacturers and with different operating systems. The right combination will yield the greatest results in security, but what combination is best? Some considerations for securing mobile devices include:
- Adoption – strict security policies can slow adoption and force users to find unsecure workarounds to do work.
- Physical Access – companies must secure the hardware, operating system and applications on all mobile devices, which have a high potential for being lost or stolen. Estimates indicate that 22% of all mobile devices will be lost or stolen with half never being recovered.
- User Awareness – many mobile devices are not secured simply because users are not educated in the risks associated with mobile usage
- Continuous connection – most mobile devices are always on and always connected to the network
Risks with Apps
The attractiveness of mobile computing comes from the wide variety of apps available to users. Download an app and in seconds a user has a new source of productivity, information or entertainment. This situation presents two major problems: malware and app vulnerabilities.

Malware is code used to compromise the security of a mobile device. An app can be entirely malware or have a portion of its code which is malware. Malware can be attached to legitimate apps and can be triggered in any number of ways. The most common forms of malware in mobile computing are ‘free versions of paid apps’ where a legitimate app is modified to allow SMS messaging or export sensitive data. Malware is more significant on the Android platform, which is the most common operating system for mobile devices.
Mobile apps created or customized by corporations for internal use can have unintentional flaws. These vulnerabilities can expose data stored on the device or allow the device to be otherwise compromised by an attacker. The risk is compounded when users are allowed to use company-owned devices to search the web or download public accessible apps which may have similar vulnerabilities.
Risks with Mobile Environment
Traditional PC asset inventory has a 4 to 6-year hardware cycle, while consumer mobile devices will evolve and turnover in 2-3 years. The frantic pace of mobile development must be counteracted with a well-established inventory and platform management capability within the company to recognize and establish security protocols for any combination of device hardware, operating system and app. IT concerns increase in the following areas:
- User device control – employees may demand a convergence of work and personal use on mobile device, which can lead to less overall control over actual usage for IT departments
- Request fulfillment – getting suitable, up-to-date, devices into the hands of employees will prove daunting. This is compounded as the use of company approved paid applications become available to employee use.
- Service Desk training – Service desks will need to be trained in all approved hardware and software platforms allowed on company-owned devices
- User expectations – more effort in setting and managing expectations for the employee assigned a mobile device.
The value for greater control over company-owned mobile devices is highlighted by a recent California case involving the iPhone of San Bernardino shooter Rizwan Farook. The U.S. government demanded that Apple, the phone’s manufacturer to unlock the device so they can get to the data as part of their investigation. This case could have been avoided if the owner of the iPhone, Farook’s employer, installed a MDM solution on the phone. The problem is compounded by the fact the employee does have a MDM to install but Farook’s department didn’t enforce its use.
Value of Mobility Management and Security
Mobile Device Management (MDM) is essential to any IT policy regarding or impacted mobile computing. The focus of MDM is to optimize the functionality and security of the mobile device while protecting corporate assets, particularly data. A number of MDM software packages are available for corporation, or a customized program can be developed to match corporate goals. MDM solutions establish a unified, secure mobile network for the company.

Here are a few security oriented benefits for organizations that leverage MDM capabilities for company owned devices connecting to their corporate network:
- Regulatory Compliance – compliance necessitates that unauthorized mobile devices be restricted access to corporate data and confirmation of network integrity.
- Remote Management of Users and Devices – monitoring and management of users and devices increases security protection and health on all authorized devices and enables the company to disconnect or disable unauthorized users or devices.
- Controlled Device Updates – ensures all devices remain up-to-date, maintaining a stronger defense against potential security incidents.
- Application Control – enables the company to control and regulate what applications are allowed on the device, thus protecting against possible malware or software vulnerability problems.
- Security Policy Enforcement – security policies for the entire IT infrastructure can be extended to mobile devices reducing the deviations in implementation, such as password requirements and access control.
- Data Backup and Restore – corporate data located on mobile devices can be automatically backed up to ensure business continuity should the device be lost or stolen.
- BYOD Support – MDM enables security support across multiple platforms regardless of hardware or operating system.
The high probability of lost and stolen devices is a major issue for many corporations. MDM solutions have several possible solutions to counteract this problem; from tracking functions to locate lost devices to remote data wiping of the device.
Still, the greatest threat to mobile security is the user. The threat increases as users take more ownership of the device and expect more freedom to use the device for personal use. MDMs can restrict what apps are available for the user; ensuring that only approved apps are installed. Partitions may be established to separate corporate use from personal use. Data usage plans can become expensive when devices are used for social media and game apps. MDMs can place limits on these activities, or simply track data usage for a variety of apps to identify opportunities to reduce costs.
Establishing a Proper Environment for Mobility

Security begins with planning. As more employees demand the ability to work remotely or away from their stationary desks, mobile computing solutions will be expected. Companies should do the following to secure devices assigned to employees:
- Identify and investigate different scenarios for mobile computing, particularly the benefits and risks for each scenario. (The image above identifies some scenarios to consider)
- Procure a mobile device management solution.
- Establish a security baseline which minimally enforces industry standard security policies.
- Certify hardware and operating systems based on security baseline.
- Define trusted and untrusted device access.
- For critical business apps, ensure stringent authentication and access control is in place
- Ensure the organization is continually aware of risks associated with mobile computing.
In addition, companies must address the risks associated with apps found on mobile devices. They should:
- Install mobile anti-virus programs.
- Extend security processes to cover development of in-house app development or procurement.
- Utilize an in-house app store and mobile app management to manage apps.
- Enable data sharing between corporate devices.
- Maintain processes to install app updates or patches in a timely manner.
- Continually assess the need for new apps to improve productivity and security.
- Enforce support processes to wipe data from decommissioned devices.
- Establish a self-service knowledge base for employees regarding issues with hardware and software relevant to the company.
Mobile computing is an opportunity and a threat to companies. Does the benefit of mobilizing the workforce outweigh the potential exposure of corporate data? The answer is based on the company’s commitment to mobile security and willingness for long-term investment in advanced cloud-based Mobile Device Management solutions such as Codeproof. Don’t let your mistake be an example to others.

